⏲️ Estimated reading time: 4 min
WHM Background Process Killer HelpZone Insights
The WHM Background Process Killer actively detects, terminates, and notifies administrators about unauthorized background processes running on a server. This feature helps prevent abuse, secure resources, and mitigate threats such as IRC bots, proxy servers, sniffing tools, and malware.
Difficulty: Easy
Why Use WHM Background Process Killer?
Many malicious users and attackers exploit background processes to:
- Run IRC servers and bots, which can be used for DDoS attacks.
- Set up proxy services to hide their identity or engage in illegal activities.
- Deploy sniffers to capture sensitive network data.
- Run automated spam tools, leading to server blacklisting.
By enabling this feature, you automatically detect and eliminate these processes before they cause harm.
How WHM Background Process Killer Works
- WHM monitors running processes on your server.
- If a blocked process is detected, WHM immediately terminates it.
- An email notification is sent to the administrator, providing details of the blocked process.
- This feature ensures that malicious or unauthorized processes do not consume resources or compromise security.
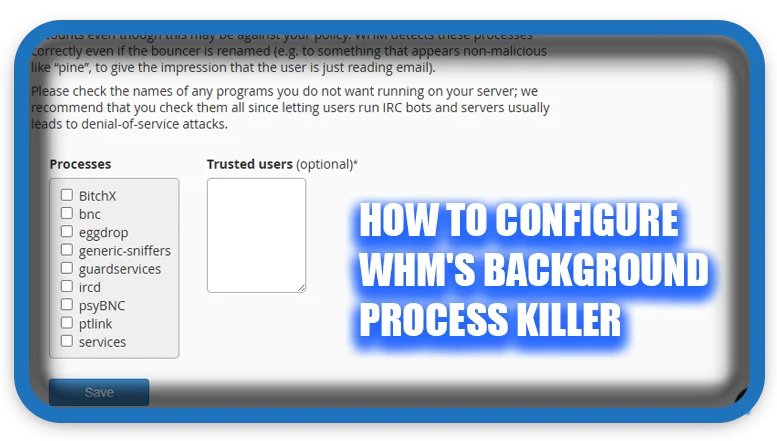
Key Processes to Monitor & Kill
WHM provides a list of common malicious or potentially harmful background processes:
1. IRC-Related Processes (Often Used for Botnets & DDoS)
- BitchX – An IRC chat client, often abused by attackers.
- ircd – An IRC server daemon, commonly used for unauthorized chat servers.
- psyBNC – An IRC bouncer that helps users stay connected, often used to evade detection.
- bnc – A proxy tool used in IRC communication.
- ptlink – An IRC-related process that can be misused.
2. Sniffing & Hacking Tools
- generic-sniffers – Used to capture and analyze network packets.
- guardservices – Can be associated with monitoring tools, but often used for stealthy activities.
3. Other Potentially Dangerous Processes
- eggdrop – A popular IRC bot, often misused for spam or attack automation.
- services – A generic name that can be used to disguise malicious services.
👉 Recommendation: Enable all process blocks unless you have a specific reason to allow them.
How to Configure WHM Background Process Killer
1: Access the Feature
- Log into WHM as the root user.
- In the left menu, search for “Background Process Killer”.
- Click on “Background Process Killer” under the Security Center.
2: Select Processes to Kill
- Check the box next to each process you want to block.
- Best practice: Enable all process blocks to maximize security.
3: Enable Email Alerts
- Check the box for “Send an email when a process is found”.
- Enter your admin email address to receive notifications.
4: Save & Apply Settings
- Click “Save” to activate the settings.
- WHM will now automatically monitor, kill, and notify you when these processes are detected.

Best Practices for WHM Security
To further enhance security, it is essential to follow these best practices:
1️⃣ Scan for malware using tools like Maldet or ClamAV. This proactive approach not only helps detect threats but also removes them before they cause damage.
2️⃣ Regularly review logs (/var/log/messages, /var/log/secure) for unusual activity. By doing so, you can quickly identify potential threats and take action before they escalate.
3️⃣ Use CSF (ConfigServer Security & Firewall) to block malicious connections. Consequently, this reduces unauthorized access attempts and enhances overall security.
4️⃣ Disable unused ports to prevent unauthorized access. Otherwise, hackers could exploit open ports, leading to security breaches.
5️⃣ Keep WHM & cPanel updated to patch security vulnerabilities. Since updates often include security fixes, it is crucial to keep your software up to date. This helps protect against the latest threats and ensures system stability.
Final Thoughts
The WHM Background Process Killer is a must-have security feature for any server administrator. By proactively blocking and terminating unwanted processes, it helps reduce server abuse, prevent hacking attempts, and maintain system integrity.
Would you like further assistance in optimizing your WHM security settings? 🚀
Only logged-in users can submit reports.
Discover more from HelpZone
Subscribe to get the latest posts sent to your email.